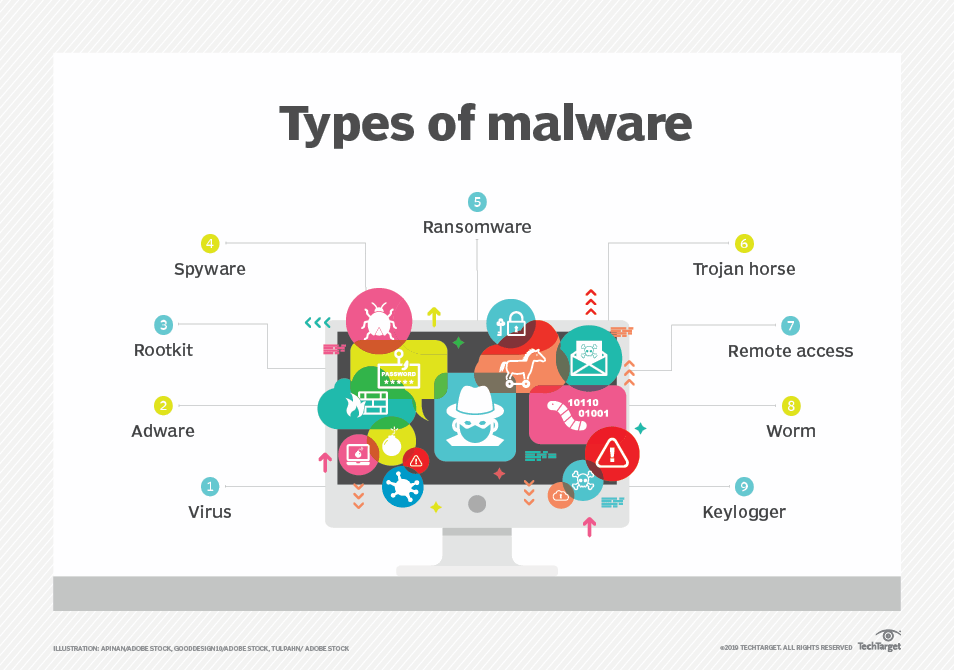
Understanding Malware and its Types
Malware includes a wide range of software that has malicious intent. Malware is not software that you would knowingly purchase or download and install. Instead, it is installed onto your system through devious means. Infected systems give various symptoms, such as running slower, starting unknown processes, sending out email without user action, random reboots, and more.You might hear people use the term virus to describe all types of malware, but that isn’t accurate. A virus is a specific type of malware, and malware includes many other types of malicious software, including worms, logic bombs, Trojans, ransomware, rootkits, spyware, and more.
Viruses
A virus is a set of malicious code that attaches itself to a host application. The host application must be executed to run, and the malicious code executes when the host application is executed. The virus tries to replicate by finding other host applications to infect with the malicious code. At some point, the virus activates and delivers its payload. Typically, the payload of a virus is damaging. It may delete files, cause random reboots, join the computer to a botnet, or enable backdoors that attackers can use to access systems remotely.
Worms
A worm is self-replicating malware that travels throughout a network without the assistance of a host application or user interaction. A worm resides in memory and is able to use different transport protocols to travel over the network. One of the significant problems caused by worms is that they consume network bandwidth. Worms can replicate themselves hundreds of times and spread to all the systems in the network. Each infected system tries to locate and infect other systems on the network, and network performance can slow to a crawl.
Logic Bombs
A logic bomb is a string of code embedded into an application or script that will execute in response to an event. The event may be a specific date or time, when a user launches a specific
program, or any event the programmer decides on.A logic bomb executes in response to an event, such as when a specific application is executed or a specific time arrives.
Backdoors
A backdoor provides another way of accessing a system, similar to how a backdoor in a house provides another method of entry. Malware such as Trojans often install backdoors on systems to bypass normal authentication methods.Application developers often code backdoors into applications, but this practice is not recommended. For example, an application developer might create a backdoor within an application intended for maintenance purposes. However, if attackers discover the backdoor, they can use it to access the application.
Trojan
A Trojan appears to be something useful but includes a malicious component, such as installing a backdoor on a user’s system. Many Trojans are delivered via drive-by downloads. They can also infect systems from rogueware, pirated software, games, or infected USB drives.
Botnets
A botnet combines the words robot and network. It includes multiple computers that act as software robots and function together in a network (such as the Internet), often for malicious
purposes. The computers in a botnet are called zombies.Bot herders are criminals who manage botnets. They attempt to infect as many computers as possible and control them through one or more servers running command-and-control software. The infected computers periodically check in with the command-and-control servers, receive direction, and then go to work. The user is often unaware of the activity.Most computers join a botnet through malware infection. For example, a user could downloadpirated software with a Trojan or click a malicious link, resulting in a drive-by download. The malware then joins the system to a botnet.
Some of the instructions sent by the command-and-control servers include:
- Send spam.
- Launch a distributed denial-of-service attack.
- Download additional malware, adware, or spyware such as keyloggers.
Rootkits
A rootkit is a group of programs (or, in rare instances, a single program) that hides the fact that the system has been infected or compromised by malicious code. A user may suspect something is wrong, but antivirus scans and other checks may indicate everything is fine because the rootkit hides its running processes to avoid detection.
In addition to modifying the internal operating system processes, rootkits often modify system files such as the Registry. In some cases, the rootkit modifies system access, such as removing users’ administrative access.Rootkits have system-level access to systems. This is sometimes called root-level access, or kernel-level access, indicating that they have the same level of access as the operating system.
Spyware
Spyware is software installed on users’ systems without their awareness or consent. Its purpose is often to monitor the user’s computer and the user’s activity. Spyware takes some level of control over the user’s computer to learn information and sends this information to a third party. If spyware can access a user’s private data, it results in a loss of confidentiality.
Some examples of spyware activity are changing a user’s home page, redirecting web browsers,and installing additional software, such as search engines. In some situations, these changes can slow a system down, resulting in poorer performance.
Adware
When adware first emerged, its intent was usually to learn a user’s habits for the purpose of targeted advertising. As the practice of gathering information on users became more malicious, more people began to call it spyware. However, some traditional adware still exists.A common type of adware is pop-ups. For example, while you are visiting a site, another
browser window appears, or pops up, with an advertisement. These pop-up windows aren’t malicious, but they are annoying.Sometimes pop-ups can be helpful. As a legitimate example, my online bank has interest-rate information that I can view. When I click on this link, it pops up another window showing the interstate information without taking me away from the current page I’m viewing.
Ransomware
Ransomware is a type of malware that prevents or limits users from accessing their system, either by locking the system’s screen or by locking the users’ files unless a ransom is paid. More modern ransomware families, collectively categorized as crypto-ransomware, encrypt certain file types on infected systems and forces users to paythe ransom through certain online payment methods to get a decrypt key.
Well known attacks
DOS attack
A denial of service is an attack intended to make a computer’s resources or services unavailable to users. In the other words ,it prevents a server from operating or responding to normal requests.DOS attack come from single attacker.
SYN flood attack
It is a common dos attack used against servers on the internet,it disrupts the TCP handshake process and can prevent legitimate client from connecting, In syn flood attack ,attacker never completes the handshake by sending the ACK packet. Additionally ,the attacker sends a barrage of SYN packets,leaving the server with multiple half-open connections.
DDOS attack
A denial-of-service (DoS) attack is an attack from one attacker against one target. A distributed denial-of-service (DDoS) attack is an attack from two or more computers against a single target.
DDoS attacks often include sustained, abnormally high network traffic on the network interface card of the attacked computer. Other system resource usage (such as the processor and memory usage) will also be abnormally high. The goal of both is to prevent legitimate users from accessing services on the target computer. Many DoS and DDoS attacks attempt to consume resources on the target computer. For example, a SYN (synchronize) flood attack consumes memory resources by flooding a system with half-open connections.
Brute Force Attacks
A brute force attack attempts to guess all possible character combinations.it is a trial and error method in this multiple login failures amy be followed by successful login. One of the best
protections against offline brute force attacks is to use complex passwords. Account lockout policies (also covered in Chapter 1) are effective against online brute force attacks.
ARP(ADDRESS RESOLUTION PROTOCOL)
The MAC address is the physical address, or hardware address, assigned to the network interface card (NIC). ARP resolves the IP addresses of systems to their hardware address and stores the result in an area of memory known as the ARP cache.
TCP/IP uses the IP address to get a packet to a destination network. Once the packet arrives on the destination network, it uses the MAC address to get it to the correct host. ARP uses two primary messages:
ARP request. The ARP request broadcasts the IP address and essentially asks, “Who has this
IP address?”
ARP reply. The computer with the IP address in the ARP request responds with its MAC address. The computer that sent the ARP request caches the MAC address for the IP. In many operating systems, all computers that hear the ARP reply also cache the MAC address.
ARP Poisoning Attack
Address Resolution Protocol (ARP) poisoning is an attack that misleads computers or switches about the actual MAC address of a system.
Zero-Day Attacks
A zero-day attack is one that exploits an undocumented vulnerability. Many times, the vendor isn’t aware of the issue. At some point, the vendor learns of the vulnerability and begins to write and test a patch to eliminate it. However, until the vendor releases the patch, the vulnerability is still a zero-day vulnerability.
Buffer Overflows and Buffer Overflow Attacks
A buffer overflow occurs when an application receives more input, or different input, than it expects. The result is an error that exposes system memory that would otherwise be protected and inaccessible. Normally, an application will have access only to a specific area of memory, called a buffer. The buffer overflow allows access to memory locations beyond the application’s buffer, enabling an attacker to write malicious code into this area of memory. As an example, an application may be expecting to receive a string of 15 characters for a username. If input validation is not used and it receives more than 15 characters, it can cause a buffer overflow and expose system memory.
Buffer overflows occur when an application receives more data than it can handle, or receives unexpected data that exposes system memory. Buffer overflow attacks often include NOP instructions (such as x90) followed by malicious code. When successful, the attack causes the system to execute the malicious code. Input validation helps prevent buffer overflow attacks.
SQL Injection Attack
SQL is the structure query language which is used to access database of application like user name , password, and permission.
SQL Injection (SQLi) refers to an injection attack wherein an attacker can execute malicious SQL statements (also commonly referred to as a malicious payload) that control a web application’s database server (also commonly referred to as a Relational Database Management System – RDBMS). Since an SQL Injection vulnerability could possibly affect any website or web application that makes use of an SQL-based database, the vulnerability is one of the oldest, most prevalent and most dangerous of web application vulnerabilities.
How SQL Injection works
In order to run malicious SQL queries against a database server, an attacker must first find an input within the web application that is included inside of an SQL query.
In order for an SQL Injection attack to take place, the vulnerable website needs to directly include user input within an SQL statement. An attacker can then insert a payload that will be included as part of the SQL query and run against the database server.
Cross-Site Scripting
It is one of the most common application-layer web attacks.
To check if the site is vulnerable or not, attacker put some client-side scripting languages, such as HTML and JavaScript.
Cross-site scripting (XSS) is another web application vulnerability that can be prevented with input validation. Attackers embed malicious HTML or JavaScript code into an email or web site
error message. If a user responds to the email or error message, it executes the code. Many times, this gives the attacker access to user cookies or other information about the user.
Cross-Site Request Forgery (XSRF)
Cross-site request forgery (XSRF or CSRF) is an attack where an attacker tricks a user into performing an action on a web site. The attacker creates a specially crafted HTML link and the user performs the action without realizing it.
Phishing
Phishing is the practice of sending email to users with the purpose of tricking them into revealing personal information or clicking on a link. A phishing attack often sends the user to a
malicious web site that appears to the user as a legitimate site.
The classic example is where a user receives an email that looks like it came from eBayPayPal, a bank, or some other well-known company. The “phisher” doesn’t know if the recipient has an account at the company, just as a fisherman doesn’t know if any fish are in the water where he casts his line. However, if the attacker sends out enough emails, the odds are good that someone who receives the email has an account.
The email may look like this:
“We have noticed suspicious activity on your account. To protect your privacy, we will suspend your account unless you are able to log in and validate your credentials. Click here to
validate your account and prevent it from being locked out.”
Phishing is a technique that deceit people to obtain data from users. The social engineer tries to impersonate genuine website webpage like yahoo or face-book and will ask the user to enter their password and account ID.
It can be prevented by
· Having a guard against spam
· Communicating personal information through secure websites only
· Download files or attachments in emails from unknown senders
· Never e-mail financial information
· Beware of links in e-mails that ask for personal information
· Ignore entering personal information in a pop-up screen
A technique used to scam people for information by impersonating a genuine site like Facebook or Hotmail, to lure the user into entering their personal account and password information.
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. Attacker sends malware through email (trick user to click on a particular link) and once victim click on the link the malware gets installed to their system.
Spear Phishing
Spear phishing is a targeted form of phishing. Instead of sending the email out to everyone indiscriminately, a spear phishing attack attempts to target specific groups of users, or even a single user. Spear phishing attacks may target employees within a company or customers of a company.
Whaling
Whaling is a form of spear phishing that attempts to target high-level executives.
Vishing
Vishing attacks use the phone system to trick users into giving up personal and financial information. It often uses Voice over IP (VoIP) technology and tries to trick the user similar to other phishing attacks. When the attack uses VoIP, it can spoof caller ID, making it appear as though the call came from a real company.
Privilege Escalation
Privilege escalation occurs when a user or process accesses elevated rights and permissions.
When attackers first compromise a system, they often have minimal privileges. However, privilege escalation tactics allow them to get more and more privileges.




